Highly sensitive workloads require greater security controls, particularly when running on shared or managed infrastructure. One solution is confidential computing where workloads run inside an encrypted enclave virtual machine (VM) isolated from the underlying physical hardware, operating system, hypervisor, and other VMs using technology such as Intel TDX. This robust security boundary increases VM security, protecting sensitive data even if attackers compromise the physical host.
However, data entering or leaving the enclave may still be at risk as it passes through a network interface or system bus to other services. Arqit’s quantum-safe Symmetric Key Agreement Platform (SKA-Platform™) allows services running within an enclave to create symmetric encryption keys that cannot be cracked, even by a quantum computer. This ensures data is encrypted securely before it leaves the enclave boundary. The data can be shared with other enclaves running on the same or different hosts with full end-to-end encryption. Encryption keys are ephemeral and never shared outside of the enclave.
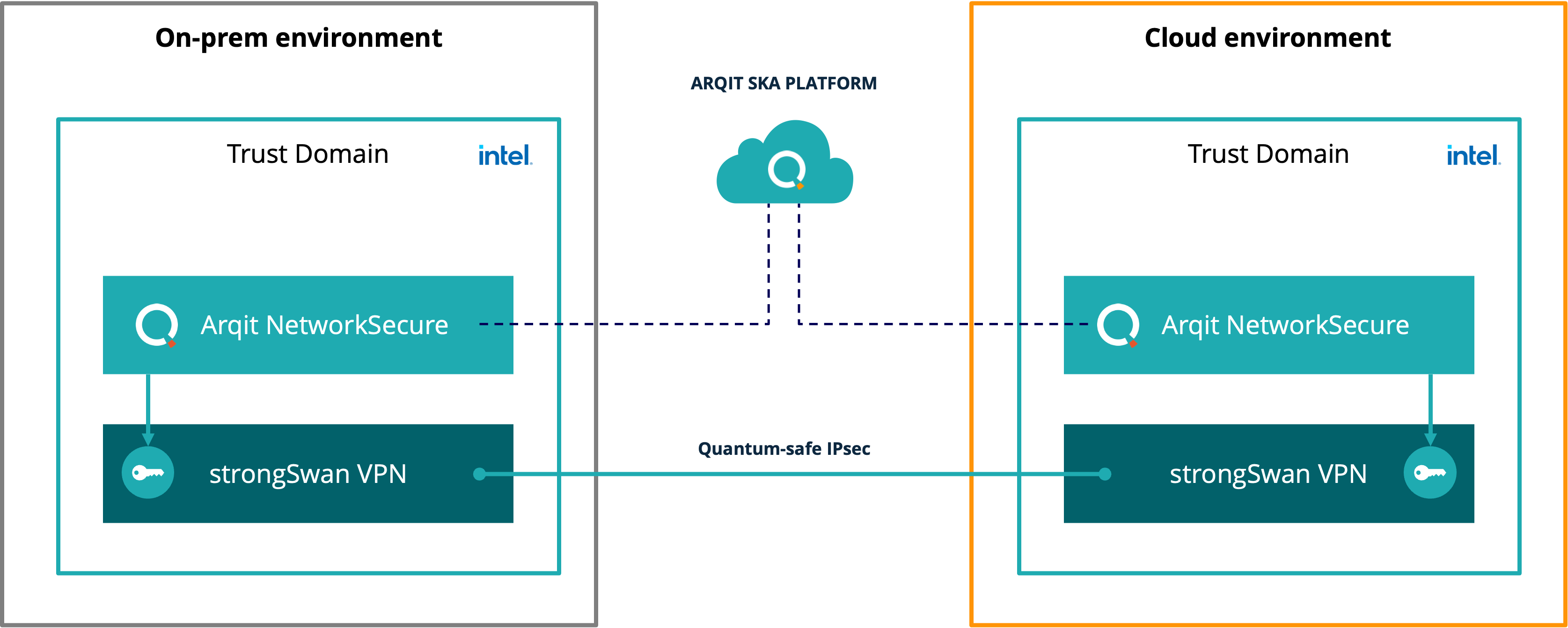
Figure 1: Example of Arqit NetworkSecure running inside a Trust Domain (enclave) provides quantum-safe symmetric keys to a strongSwan VPN client. The keys are ingested by the client and used to secure the IPsec tunnel between the clients. Data is protected from the physical host both in use inside the TD and while in transit between environments.
For customers, this means sensitive data in workloads like AI or financial systems is not only protected in use on the host, but also in transit as it’s distributed to other services. This is particularly relevant for industries like finance, healthcare, or government that handle regulated customer data but who want the flexibility and power of public cloud. It also reduces the liability of the cloud provider itself by removing liability associated with data exfiltration or host misconfiguration.
Beyond data-in-use encryption, Intel TDX also provides remote attestation capabilities, meaning workloads can prove they are running within an enclave and confirm other hosts are also using Intel TDX. This reduces the chance of man-in-the-middle attacks or data poisoning by rogue endpoints and ensures that workloads never share data with environments without Confidential Computing. Arqit’s own symmetric- based active authentication service augments the PKC-based approach offered by attestation services, providing quantum-secure authentication in addition to data security.
Attestation can also be used to verify that NetworkSecure is running unmodified by a third party, and that information could be shared with other TDs through the quantum-safe data link. This removes the risk of tampering and ensures the integrity of Arqit’s software running inside the enclave.
Key benefits for customers:
- Data-in-use and data-in-transit protection for highly sensitive workloads, especially on shared infrastructure.
- Simple to use and deploy
- Independent attestation provided by Intel Tiber Trust Authority
- Encryption keys are never visible to the users outside the enclave, maintaining full data confidentiality and ownership
- For hosting providers, prevent inadvertent data leaks, reduce liability, and offer your customers quantum-safe data security with minimal customer configuration.
We believe the combination of quantum-safe data-in-transit security offered by Arqit combined with the confidential computing capabilities of Intel TDX provides a powerful, holistic solution to data security.
